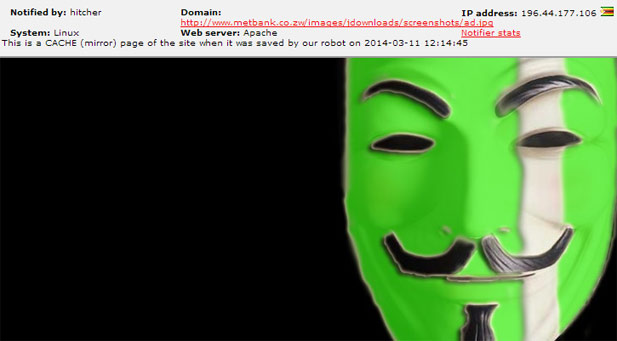
 A number of local website were in the past 3 months breached by hackers, amoung them the MetBank website, ZiFMStereo.co.zw, Pastel.co.zw, Chips.co.zw and other less familiar brands. The websites were breached on different occasions with the latest being that of ZiFMStereo, which was attacked two days ago.
A number of local website were in the past 3 months breached by hackers, amoung them the MetBank website, ZiFMStereo.co.zw, Pastel.co.zw, Chips.co.zw and other less familiar brands. The websites were breached on different occasions with the latest being that of ZiFMStereo, which was attacked two days ago.
Most of the websites have been fixed, except for the Metbank’s which we notice is actually now offline.
Like other such breaches locally, these don’t seem to be deliberately targeted at the companies but more a result of random attacks on vulnerable targets. The attacks also didn’t hit the front page, but just injected malicious files to the web servers.
Here are some screenshots from some of the breached websites:
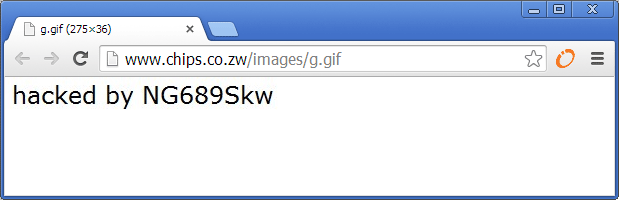
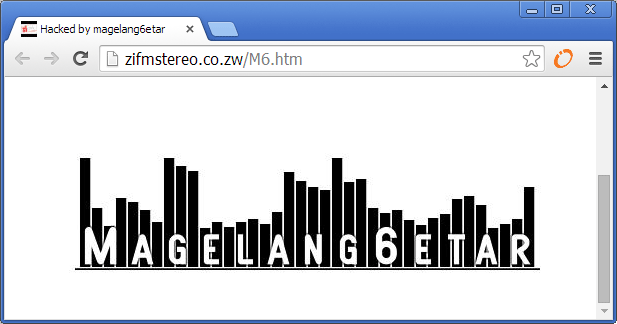
Metbank is a local bank. The Pastel and Chips websites both belong to Chips Computing, a local accounting software company. ZiFM Stereo is one of the most popular radio stations in Zimbabwe.

13 comments
How are the locals going to gain confidence in online payments when the banks do not have enough security to ensure the safety of their websites?
Obviously most bank keep their banking systems separated from the corporate website. Most of the time the internet banking site’s software is usually provided by a service provider who makes sure its impenetrable else a compromise on one site will mean a compromise on their other clients.
why not host with the same ‘impenetrable’ dude then?
I’d like to know 1. are those sites locally hosted? 2. What was used to build the site i.e. Joomla / Drupal / WordPress and 3. Are all those site developed in house?
Zifm website is hosted by Hosting24 from Cyprus, Metbank hosted by iwayafrica, chips and pastel hosted by yoafrica
Those slothful System Administrator’s should be sacked
Apparently they are Russian gangs that can just about do anything. No matter even if the sys admin secures all patches and vulnerabilities. It’s a headache for most firms even in the Western world with dozens security experts employed.
Izvi hazvina kuti uri SysAdmin akapenga or akapusa as long as a vulnerability is there no matter how frequent you patch up and update your sustems unongopindwa chete.
The bottom line is these companies do not take IT security seriously. This is not a sys admin responsibility. It is for a security department, eg the banks, corporates, etc. Econet had this issue but we all know how they reacted to the breaches. If the role is assigned to the SA, then it is his/her job to make that the systems being looked after are patched with required/relevant patches. Some of the breaches we see/read are based on lack of maintenance and management of such systems.
Maybe there are more important things to worry about than a website being hacked. After all, it is just a bunch of pictures and text!!
They do take security seriously, in fact Met Bank has an IT Security department. The problem as I see it is on the technical skills of these “security experts”. Most of them just used brain dumps to get certifications and lack actual security knowledge and experience
Wondering if they thought of hitting techzim as well or the site was not a high value target?
Stop building Sites using JOOMLA or any other CMS, they not secure….
@Harker All websites on the Internet are vulnerable to hacking and other exploits. There are no exceptions. how ever there are measures you can take to improve the security of your Joomla Website.
1. Change your Administrator username. Do not use “Admin” or “Administrator”.
2. Make sure your configuration.php is not writeable.
3. Always keep you Joomla upgraded to the latest version.
4. Once you have a stable site, you should change all file permissions to write protected using CHMOD (644 for files, 755 for directories). Any good FTP software should allow you to do this without having to use any scripts.
5. Ensure that there are no unneccesary files on your web server.
the list goes on and on