Image credit Pixabay
The WannaCry ransomware attack seems to have triggered a lot of cybercrime around the world – including in Zimbabwe. We notice how since then we’ve been hearing of ransomware attacks every now and again. Frankly speaking, it’s beginning to sound like some cybercrime movie but only less exciting since this time no-one is safe – now that sounds more like a horror movie.
Anyway, this morning we got an email from the Zimbabwe Information and Communication Technologies (ZICT) informing us of yet another worldwide cyber attack and it read:
A massive ransomware attack has hit computers and servers across the globe causing turmoil in its path. The latest Cyber Attack, PETYA RANSOMWARE which has reached Asia after spreading from Europe to the US overnight, hitting businesses, port operators and government systems. The attack first shut down operations in Russia, including at Russia’s biggest oil company and Ukraine before spreading to computers in Romania, the Netherlands, Norway, France, Spain, and Britain. In a matter of hours, the attack had gone global, hitting the US and India. Now, it’s also understood some businesses in Australia including the Cadbury chocolate factory in Hobart are also affected. There has been no reports in Africa.
How it spreads
The latest attack Petya ransomeware is hidden in an innocuous document sent through email. Once the user opens the attached document, it freezes a user’s computer until a “ransom” is paid in virtual currency bitcoin.
Target
Petya Ransomware Outbreak is targeting Windows systems via client & network attacks.
The Ransomware is spreading using a pseudo client-side and network service attack of a modified version of the WannaCry worm and loader. It is based on MS17-010 AND CVE 2017-0199 using multiple attack vectors which may include;
- Spreading via un-patched MS17-010 systems as per other ransomware.
- Spreading via malicious RTF documents in Office that can download and run malicious VBscript.
- Spreading to other hosts using inherited credentials as the user it is running as and connect to other Window machines using WMIC (Windows command-line control over WMI)
Interesting Information
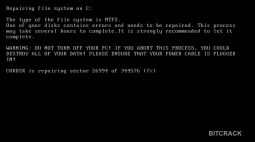
As it stands, the Ransomware masks itself as a CHKDSK scan of your computer, pretending to be searching-for and fixing errors on disk. As per the screenshot below;
However during this process it is actually encrypting your drive. The following screen once complete will be the ransomware request screen.
At this stage there is no confirmation that paying the ransom results in decryption.
We recommend the following action;
- Patch for MS17-010 & CVE 2017-0199 if you have not done so already (extremely urgent)
- Update Email scanning engines to detect malicious scripts in RTF documents (primarily).
- Notify users to be careful of email attachments with RTF extensions and/or not to open suspicious looking attachments.
If you have been infected please do not hesitate to contact us on 0772278161 or email chair@zict.org.zw
Hopefully that will be helpful to you.

4 comments
What happens if you have dual operating systems on one PC (e.g windows 10 alongside Ubuntu) . Does the ransom-ware lock both operating systems??
This malware from the description above requires Windows in order to spread and execute. It also requires a Windows file system i.e. NTFS, FAT32 and possibly FAT16 (do people still use this). Ubuntu by default would be installed on a separate Ext4 partition or if you opted for it btrfs. So the answer would be no. The Linux partition should not ordinarily intelligible to Windows adding Ext4 to the malware would significantly increase the size of the malware thus reducing stealth for what is a very small population of computer users. Besides people who dual boot are less likely to be novices who click on any and everything.
P.S who the heck uses Office and Email clients anymore anyway? The later is probably on it’s death bed.
There are still businesses out there who use licensed software and find this a cheaper option, albeit insecure.
The latest reports suggest it might not be ransomware but a virus that wipes the hard drive of affected computers. It’s only disguised as ransomware to throw off investigators. Paying the ransom also doesn’t work, the email adress where you are supposed to send the proof of payment has been closed