PGP Snowden.
So I couple of weeks ago I promised I would provide a guide to personal encryption that anyone can use with their files before they can entrust them into the hands of some unknown data company in some unknown country.
I still find it incredible that people, despite the breaches being suffered by both established companies and startups, can still find it their hearts to entrust their most private data to these Cloud Storage providers without ever bothering to find out what security measures they have in place.
What the heck is encryption anywhere?
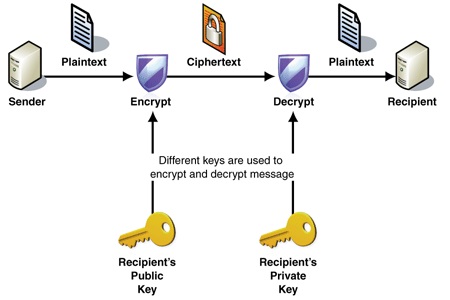
I know I am going to offend purists here, but this article was written with the humble man/woman in mind. Encryption is the translation/conversion of data into a secret or unrecognisable form. This is often done so as to protect sensitive data/information so that only authorized parties can access it.
An encrypted file will appear scrambled/muddled to anyone who tries to view it. It must be decrypted in order to be recognized. Some encrypted files require a password to open, while others require a private key, which can be used to unlock files associated with the key.
When a file is encrypted, anyone who intercepts it will have to decrypt it first before they can read it/understand it. The ease with which they can do this depends on the algorithm that was used to encrypt the file, the skill of the person or persons trying to decrypt the file and the resources that they have access to.
Needless to say therefore that not all encryption algorithms and therefore software programs are created equal. Cryptography is a course that has Doctorate programs at a lot of Universities around the world and so we are not going to waste space and time talking about all the methods of encryption that you could use. I have made all the hard choices for you and came to the sensible conclusion: You should use PGP software because:
- Edward Snowden swears by it.
- It has been ported to almost every platform under the sun.
- All these ports are generally compatible with one another. The worst mistake you could ever make is to make use of some third party encryption software and then it goes out of business and leaves you flapping in the wind and without a way to decrypt your files.
- It is open source which means the code is frequently audited by some of the best security experts out there and patched. Closed encryption software might have backdoor(s) put in by Governments, Alphabet organisations, the Illuminati and Aliens so that they can access your data without your permission.
- A lot of governments including Uncle Sam detest it which means it must be pretty good (see what I just did).
- It uses asymmetric encryption.
- There is no known instance of someone breaking PGP encryption but then again the Germans thought enigma was unbreakable.
I swear I wasn’t wearing only my underwear when I wrote this and my mom does not have a basement so I am not writing this from some subterranean level.
What is PGP?
PGP stands for Pretty Good Privacy and refers to all programs and software suites that follow RFC 4880. PGP is an encryption and decryption program that can be used to provide privacy and authenticate communications (e.g. emails), encrypt and decrypt files and directories and even entire disk partitions. It was created by Philip R. Zimmermann Jr in 1991. It is the most popular encryption software out there.
It is important to remember that while there is no known instance where PGP has been broken by cryptographic or computational means, humans are always the weak link in such instances as the breaking of the Enigma demonstrated. You can watch the movie The Imitation Game to learn all about it. You should therefore be diligent when it comes to guarding your keys and not to entrust them to some third party.
In our next installment we’ll look at PGP programs that you can use for various platforms.
Image credit: Makeuseof.com
6 comments
“…the skill of the person or persons trying to decrypt the file and the resources that they have access to..”
Salting is what stops skilled from decrypting files which is like scrambling egg or smashing it into tiny pieces then ask someone to put it back together.
Quantum computing plus few years is what you nedd to try and decrypty that is if the password or key hav not change already.
PGp is the only proven formula which was not developed with the help of Uncle Sam(NSA) hence no backdoor introduced.
I’m going to refute your comment: It is open source which means the code is frequently audited by some of the best security experts out there and patched” read about all the OpenSSL critical exploits to know that this is never the case
The problem with Open Source is that companies don’t take seriously this fundamental requirement to audit and maintain the code instead leaving it to people that are often just working on it part time as a hobby rather than giving serious coding time (and then audit time) to fix issues
I’m not against OpenSource but big companies using mission critical open source software need to get real and support these projects properly with time by releasing developers to work on the project within there work time or financially by seriously donating to the project so that they can pay developers to work on it properly
Even those tried all their life to kill opensource, Micro$oft, are now full time advocates of it!
I ve seen some DUM 4th year CS students store unhashed passwords in databas e tables and that makes this article useful.
Good point. Though I think you may be a little off topic or maybe you’re making a very common mistake. Hashing and encryption are 2 very different concepts…
Vulnerabitlity found in Windows encryption software TrueCrypt http://www.bytenny.com/post/encryption-program-truecrypt-has-a-critical-vulnerability