These days hardly a day goes by without news of some famous organisation or individual suffering some sort of cyber-security breach. With cybercrime on the rise no one, it seems, is being spared as criminals motivated by things as diverse as terrorism, money and personal revenge are on a rampage.
Zimbabweans have treated these tidings with nothing but mild interest and apart from a few sex tapes which have seen their way to the public, have remained relatively unscathed. Most people I have conversed with subscribe to the delusion that they are immune to cybercrime but the truth is if you hold your hand long enough and close enough to the fire you will eventually get burned.
These breaches are costly in both financial and reputational terms and you or your business might never recover from such a breach. The old mantra “Prevention is better than cure” comes to mind in such cases.
The truth is that while many of these breaches tend to be sophisticated and varied in nature they all seem to rely on the same ubiquitous bug; human nature. Often times the businesses that have been targeted and shamed made one human error or another that allowed their attacker to gain access to their system. While these mistakes are more complex on the service provider’s side most of these breaches on an individual basis rely on weak passwords.
Every year various blogs make a list of the most famous passwords and it seems most people never learn until its too late. Famous passwords include the word password itself or some weak variant. The Hacking Team, of all people, sused P4ssword as one of their passwords.
Some people have complex passwords that they keep within the vicinity of the machine that they are meant for, some people use their birthdays, others use the same password for everything, others use their love’s birthday. The truth is most people’s passwords are easy to guess.
I know certain morons from a certain organisation who have a Centos server that has a root account whose password they all know. It hasn’t changed in 3 years, as a result, everyone in that organisation knows the password.
Multi-factor authentication
You can avoid becoming a victim of most of these breaches by making use of multi-factor authentication. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the user’s identity for a login or other transaction.
Most people have used key blockers. In order to gain entry into your house, a person would require access to both the key blocker and the key. If a person lacks access to either one they will not be able to gain entry to your house.
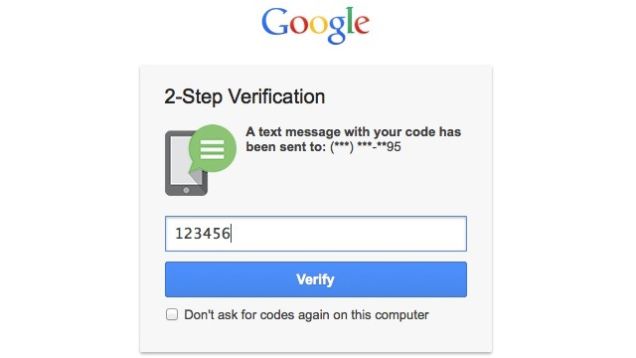
Typically, when you enable MFA you are asked to enter your phone number. Whenever you try to log in you will be prompted to enter your password as usual.
Once you have entered the correct password a one-time code is sent to your mobile via SMS or an automated call. You must enter this code to proceed and gain access to your account. With most services you have the option to enable cookies in your browser so that you can skip the code phase the next time you try to log in.
Most services on the internet now allow you to use multi-factor authentication usually in the form of two-factor authentication. Popular services like Google (which means Google+, YouTube, Gmail etc), Facebook, Amazon, Apple and Microsoft all support two-factor authentication.
Unfortunately at this stage you will have to opt in to take advantage of this feature. The folks at PC World have already penned a guide on how you can do this with most services.
Things to keep in mind
- MFA does not mean you can get lazy on your password.
- Be very careful when checking the option to skip two-factor authentication on the next login phase especially when you are using a public computer. By default, for example, Google has this option checked. I have been to an internet cafe where people have simply closed the window instead of actually login out. This is a potential Achilles heel.
- Follow the instructions carefully when using two-factor authentication otherwise you will be no safer than when using just your password to authenticate.
- It is always better to use the code generator instead of using SMS. A recent incident has left me with a very strong belief that our government may well have carte blanche access to SMS and telephone communications with little oversight. If you are as paranoid as me then you would do well to use a code generator.
MFA is a very useful tool when it comes to preventing unauthorised access to your online accounts. You should be wise and make use of it now before you suffer the inevitable breach that is coming your way.In our next instalment, we’ll look at how you can make use of two-factor authentication using your Ubuntu Desktop.