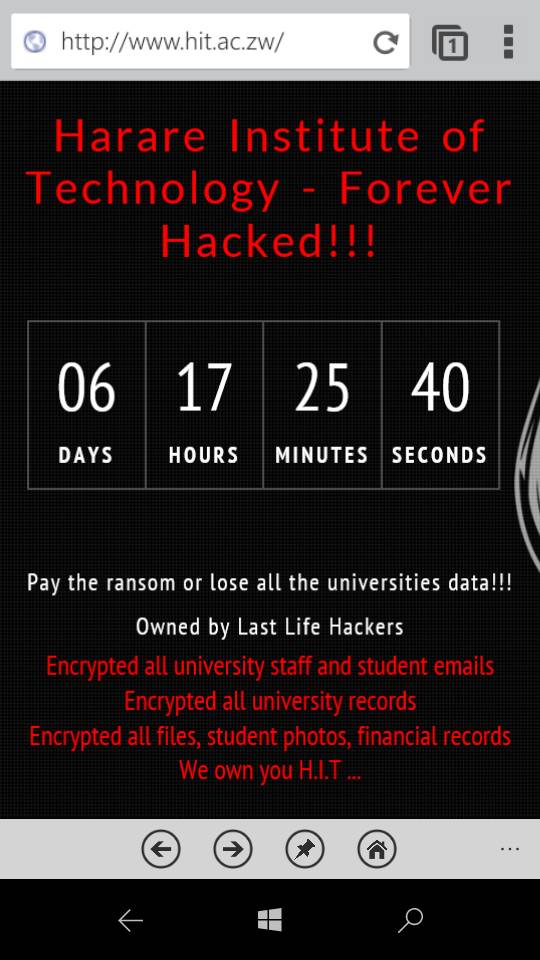
Today, on whatsapp a screenshot with the Harare Institute of Technology website being shown as hacked started circulating. We tried to open the website to see the same thing as was in the picture but it failed to load. Chances are that the website has been taken down by HIT if they’ve found out what has happened hence it’s no longer opening.
Since the website couldn’t open, we cannot say that they have been hacked as a fact because the website being down could be caused by something else and just be a coincidence. However, we also recently received the following email from the attacker.
===============================================
= Last Life Hackers =
===============================================
* RANSOMWARE LETTER *
**************************************************************************
This is not a rape,
we are not molesting you,
we are not killing anyone,
we are not setting off bombs.
This is a ransom – and this is a targetted attack.
************************************************
We have shredded and deleted all your backups eliminating
all chances of recovery.
All of your sensitive files, databases and emails have been copied to
a remote server and all local copies have been encrypted using AES-256
and the originals deleted.
We encrypted 1.3TB of University data using salted AES-256 CBC, including emails dating back to 2013, all financial records, student aid records, the entire website and 56GB worth of MySQL databases. Daily incremental backups to a bastion server were misconfigured and have not for ages(wrong IP) hence all copies of backups which were on the same machine were destroyed.
AES is a symettric encryption, meaning you will get all of your data back
if you use the same key used to encrypt the files.
We require that you pay USD$999 for the decryption key and instructions on how to recover all your data.
Send an email to onmylastlife@protonmail.com before the 27th of June 2017 or we will
delete the encryption key and terminate the email account. We will also disclose instructions on how
payment should be sent via Bitcoin.
If you contact ProtonMail resulting in the closure of the email address or fail to pay
the ransom by the 27th of June – all of your files will be lost and we will dump the decrypted 56GB gzipped database online.
Remember!, this is simply a ransom, not rape or murder.
Contact: onmylastlife@protonmail.com
Email header: H.I.T ransom settlement
Greetings!!!
***************************************************************************************
As a sign of good faith: Here is the password used to encrypt your 600GB email
backup:
To decrypt the email backup run:
ENC_PASSWORD=”P09eJWHu0VjuH17dzXCPEuk5vmYZh+vbkPVDFd2+oRn6AEOpUPhSPCM3UjFgMBMq
gFmU4n7Wm6KDLSdZ9rH5eLa2OzuiPgwvTYaA2kMnJO9PKJUT8e6u3CQ+e2rRp5po
dg==”
cd /home/backup/
for f in $(find -type f \( -name “*.ransomed” \)); do echo “Decrypting $f … “; cat “$f” | openssl enc -d -aes-256-cbc -nosalt -pass “pass:$ENC_PASSWORD” | cat > “$f.orig” ; rm -f “$f”; done;
Sent with ProtonMail Secure Email.
44 comments
lol! i thought it was just a fake warning after they defaced the site. seems they got owned here…..
Indeed
HIT should up its game in terms of cyber security
Lack of qualified personnel. They’re only good at marketing themselves as well as claiming to be a top technological institute. A mere tiger on a paper.
this has inside job written all over it
the innovation and technoprenuership university
HIT should jst Changamire from MSU
Tell dem
Oooh dear, you have no idea. They already use Changamire and he aint safe at all
paita ashaya mari ye fees apa. With alll the records the hackers have why only ask for $999?
amana $999 here
nhai nhai, vapfanha havazi serious ava. Dai vatoti vakuti $100K
Dzakapusa shuwa, $999, mari ye fees.
We are not safe anymore- people are getting more greedy by the day. However, my theory is ” Hackers are the same people who design operating systems and know all the back-doors”. We will never win the game.
Wrong – you don’t have to have written the OS to hack but an excellent knowledge of it helps. Hackers are usually sharp at both software and hardware/electronics engineering.
Inga maiti HIT has the best gurus in town.
The students are gurus the lecturers on the hand not so much
Like!!
You’ve been deceived my friend.
Hahaha balemi namcdee ngavagadzirise site kwete kuita kunge vanhu vasinga keti
@Mupfanha_wacho LOOOOL wandispaka, Balemi ngavasote kkkkkkk
TechZim you are next..backup your site before I attack it.
oNmYLastLife (We are the Serbians)
n0where.net/
Get a life
Balemi vakasara padhiri iri. Vaita vatete…
you can’t tell me that hit did not have a physical backup of the records. if thy do restore everything.
Techzim ..did you interview people from H.I.T? Or you now operating like H-Metro? So you are say if i creat a text on whatsapp saying you were hacked does that make it real?
Or you are saying everything on whatsapp is a fact
Please read what I said. It clearly stated that we cannot state that the website was hacked for a fact. I will add more information when we get it.
so basically its a rumour? The why write “Harare Institute of Technology allegedly hit with cyber attack” as if you are certain
I used the word allegedly because it is used to say that something is claimed to be the case or have taken place, although there is no concrete undeniable proof. I also stated in the article that the fact that the site is down could have been caused by something else. We have engaged people from HIT but we haven’t received a response yet.
Rufaro,I saw it yesterday morning around 6am when I tried to open it,it was hacked.
And also went there in the afternoon,asked the administration staff about it and they said yes its true it was hacked,
Dude, please buy yourself a dictionary and look up the meaning of “allegedly”
I saw it yesterday morning,there was that hacking msg,that’s true story
mmmmmmh pakaiapa
From my own understanding with experience in the industry thats just general web defacing That message is just for cyber bullin and an intrest in social engineering.
Go down on the ground and see. Systems at HIT are different , their website is just a front end system linking those systems
There is nothing spectacular on that issue. Its not even a ransomware. Thats a hack and now they are doing social engineering
i wouldnt be so sure. Today they brought the site back online for a breif moment but i couldnt access my results or emails or any of the elearning facilities except for the static home page,so yeah they hacked big time
As it is an institute of technology,they may have done it themselves in the name of experiment
..Plenty vulnerabilities on this site & can only be discovered by geniuses.. evil laugh mmmmmwaaaha ha ha ha ha 🙂
true
anyone who knows microsoft excel can hack that site
its not the $999 they are after, these guys are testing the power of the I.T security of the H.I.T…. when the ransom is paid, something big will come up and they will demand more…
common sense; watch scorpion the series
Haha guys, people are watching too much Mr Robot, Silicon Valley and Scorpion Series whatever, so many of them, just so you know this is an actual crime, and its homework which is being worked on, so most of your contributions are being collected and processed since this is a public website and a public issue.
hahahaha they apparently they want 1000 biticoin guys which is close to $2 800 000. HIT yagarira nhanzva apa. Munhu wese can now physically claim to be their graduate. Zvikwereti cancelled….kkk