Over the past few or so months, we have been at pains to teach Zimbabweans about online scams and phishing attacks, how to spot them and how to thwart them. The truth though is that these attacks are always evolving and it can be hard to spot such an attack in the wild. Nothing beats a real-world example when it comes to illustrating the cunning that goes into these attacks.
A real world example
Late yesterday, prominent journalist, Blessed Mhlanga, who is the head of news and current affairs at the News Day affiliated Heart and Soul TV Radio shared a screenshot from someone who came to their inbox claiming to be from Twitter’s Documentation Center. I am not even sure such a thing even exists. The good news is that he seemed to know that this was a trick.
Below is the screenshot of the message he received.
It’s not clear whether this was a targeted attack on the journalist or not but quite a bit is going on here. A lot of Zimbabwean public figures have been seeking verification from Twitter (the coveted blue tick) as a way to protect their personal brands, stand out from impersonators and make it harder for their accounts to get blocked.
Journalists are among those who often seek verification but it’s not clear whether Mr Mhlanga had sought to be verified in this instance. Twitter has murky rules about which accounts get verified. They say when they are considering whether or not to verify an account they consider “public interest.” It’s hard to determine what exactly that means but blue ticks are a highly coveted badge.
In this case, it seems the phishing message was socially engineered to target an account with a lot of followers and making it sound like it was from Twitter. The aim was pretty simple, to steal the account’s credentials. Accounts with a lot of followers are often sold on the dark web and on Reddit. They are bought by spammers and people who usually want to carry out more phishing/scamming attacks on the unsuspecting followers of the compromised accounts. An example is the 2020 Twitter account hijacking scam.
What was supposed to happen in this phishing attack
In this case, the attempt never really took off but let’s look at what was supposed to happen. The victim was supposed to be thrilled that they had finally been offered an opportunity to be verified. they would then click on the URL included in the link in order to verify their account. Just to be clear, Twitter does require you to apply in order to be verified although the process does not require you to login again.
If the victim had clicked on the included shortened URL they would have landed on that page and depending on the device they wouldn’t even have noticed that they were no longer on Twitter. Checkout that page’s URL
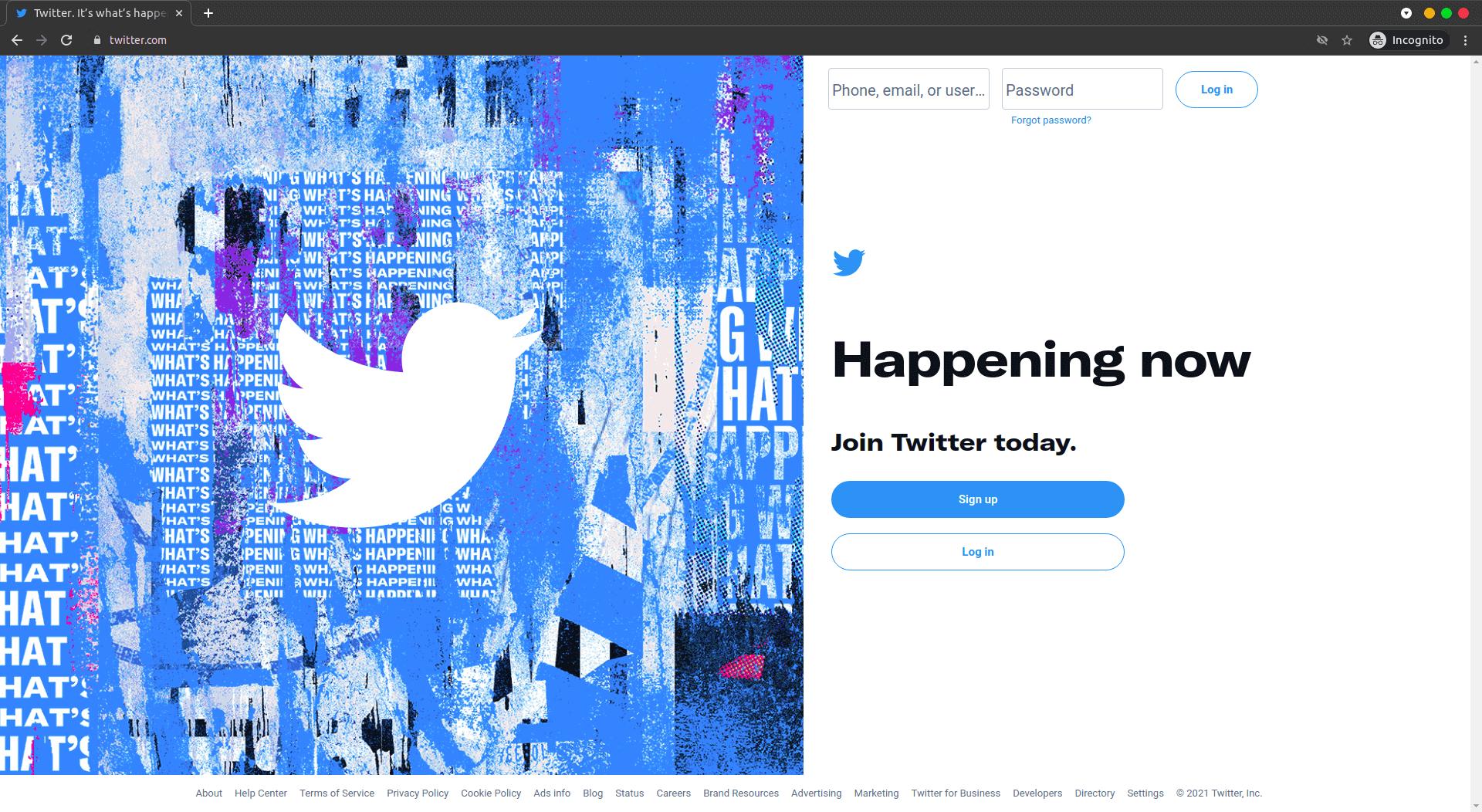
That is clearly not a Twitter domain name but if you were not paying attention you wouldn’t even notice. The Twitter log in page used to look like that and some of its pages, like those you see when the login fails or they want you to confirm some details look like that but below is the current Twitter real login page.
Now for the fun part, the reason why the page looks a lot like Twitter’s own pages is because it is one of Twitter’s own pages for all intents and purposes. The attacker achieved this by loading CSS and JavaScript resources straight from Twitter’s own servers. The gall!
So even if Twitter changed their schemes and such the phishing page would still strongly resemble Twitter’s own pages. The only thing the attacker changed was what happens when the login button is clicked. As soon as that is done, the victim’s Twitter user name, email/phone and password would be send to the attacker’s server where it would be stored and the victim will be redirected back to the real Twitter in an instant and they would be none the wiser. As far as the victim is concerned they were temporarily logged out and logged back in.
Another thing is that the Phishing website makes use of a URL shorterner. That trick serves two purposes here:
- It masks the actual target domain, URL shorteners are often used on Twitter because historically Twitter’s character limit used to apply to the characters in a URL as well. So you didn’t want a long URL to limit whatever message you had. These days any URL is counted as 23 characters no matter how long it is but people still use shorteners for presentation purposes.
- Each shortened URL appears tagged with a unique ID associated internally with the victim. The use of an ID might be for many reasons. For example the attacker might use it for A/B testing in order to determine what strategies worked and what did not. For example if they have many social engineering tricks they employ to lure victims they can gauge the efficacy of each attack. Or it could be a paid campaign, someone paid the attacker to compromise the victim and this is an internal way of keeping tabs on things.
The attacker’s mistakes
This was a fairly sophisticated attack but it was easy to spot. The most glaring mistake was in the original messages:
- The attacker made a mistake when choosing the name to give to the purported origin of the message. Twitter Documentation Center, what the heck is that? They could have said Twitter Help Center or something much more plausible. Maybe I am missing something here as I never attempted to get my own account verified. It could well be that there is indeed a mysterious Documentation Center in charge of the process.
- The second mistake was the blue tick used here. It appears to have a white background which stands out like a sore thumb on the victim’s phone. The victim is using dark mode. The attacker should have used a transparent png file which would have been at home on any device regardless of whether the phone is in dark mode or not.
Further mistakes were made by the attacker including:
- The bizarre URL screens phishing attack as it is long and has a .RU extension. Nothing says phishing like a .RU. It’s just not common outside Russia and Twitter certainly doesn’t use it. In fact the attacker chose to go with a free domain which clearly shows where the malicious page is hosted. Something like twitter.tld where tld is a little know extension would have been more subtle and probably more successful.
- The attack only works if you click the login button and not on the other links. Try to change the language and the attack fails, click on forgot password and the attack fails.
So it would have been possible to ramp this up with a little more effort and make it a really sophisticated attack.
How to thwart such an attack?
First do not respond to a message that says your application was successful when you clearly never applied for anything. Even if it’s one of those things you have wanted.
Secondly, turn on two-factor authentication. In fact, you should always turn on two-factor authentication when it’s available. Avoid using SMS for two-factor authentication. It’s very vulnerable if the attacker can have access to your SMS message e.g. journalists and activists when they are attacked by state linked actors. So use something like Google Authenticator.
Hopefully you have learnt something from our little Sunday expose.

What’s your take? Cancel reply