This review was never intended to be and actually never on my to do list. It came about through what I consider a nifty turn of events.
Recently, I dusted off an old laptop from storage which I had grudgingly given up nearly a year ago over a power pack issue.
To my surprise within minutes of getting on my network I received an email notification that my good old machine had been spotted somewhere in cyberspace.
“Cyberspace” turned out to be a physical location right next to where I was seated somewhere in Avondale West in Harare. How cool is that one year later!
It then became apparent that 11 months ago I signed-up for Prey.
Eleven months later, Prey delivered on its promise leaving me to think it’s an incredibly powerful application which could not allow a long out of mind trail to turn cold had my laptop really been stolen.
I then proceeded to extensively explore the application avoiding reading other people’s reviews online so as to present this uninfluenced review of my own.
What is Prey?
Prey is a theft protection application that is primarily designed to help recover stolen or missing devices such as desktop computers, tablets and mobile phones.
Currently, it is limited to iOS and Android for tablets and phones.
In plain English prey is synonymous with hunt, catch and seize which inevitably means the software application can be wide-ranging to include things it’s not built with in mind and therefore extraneous to this review.
How does it work?
By going to Prey, users can create an account online and by choosing between a free plan or paid plan, then gain access to a dashboard.
The free plan can track up to 3 devices. The paid plan at $5 per month can track same number of devices but with additional features.
There is also an additional paid plan that tracks 10 devices at $15 per month. There is one more paid option that allows setting of a custom number of devices and this is designed for organisations.
On the free plan you can remotely sound a 30 second loud alarm, send a message to the device, or lock the device.
Sending an alarm forces the device to ring at a very high pitch even when volume is turned off which is great say phone or tablet suddenly goes missing in a classroom or conference room.
Sending a message pop-up the message on the device desktop and locking the device locks desktop access and requires the unauthorized user to insert a password which you set remotely from the dashboard.
Adding devices to your dashboard is fairly straightforward. You will need to install the Prey Anti Theft app from Google play or App Store in order to link your devices to your dashboard.
For both desktop and mobile devices, Prey avoids giving itself away to the would be thief by not showing any icons or how to easily remove it.
Reporting
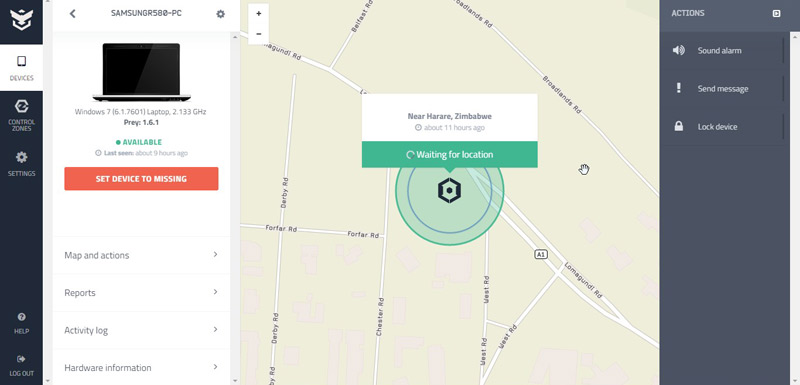
The reporting system is very impressive. The dashboard tracks your devices and for devices set to “missing” it generates serialised reports at 10 minute intervals on free plans and every two minutes for paid plans.
The interval reports are so detailed they include screenshots and pictures which the Prey agent running on your device takes using the device’s own inbuilt camera.
This way the software agent hopes to capture the face of the thief or the surrounding environment which you could present to the police to help with investigations.
Pictures produced are entirely depended on how good the device camera is.
The agent’s use of the camera is extremely smooth it makes no clicking sounds or other such when taking pictures and screenshots which are then included in the reports.
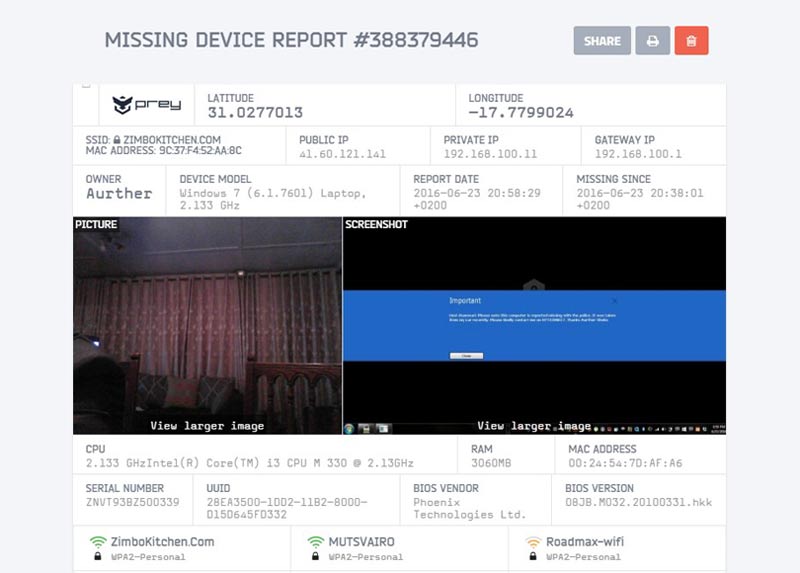
The reports provide pinpoint location of missing device by providing latitude and longitude coordinates which can be used in a handheld GPS device to take authorities within meters of the thief’s doorstep.
Prey reporting also includes the serial number of the device which is essential in proving the device is yours against your purchase documentation.
Other data in the report include the network connecting the device at the time of reporting and other networks in the vicinity. All this data put together is very helpful in leading to a recovery and tying the offender to the crime.
Pros
– This review is based on a free plan which I think is still powerful enough to help recover a missing or stolen device.
– Prey is extremely efficient in giving alerts by email and in the dashboard itself.
– It gives device owner powerful features such as wiping out data and restoring to factory settings preventing unauthorized user accessing sensitive information
– It permanently damns the old fashioned way which never really took off of having to open computer to insert a GSM sim card for tracking risking loosing your warranty.
– Control Zones available under paid plans and for mobile devices only, are a geofencing feature allowing you to set areas on a map so that you are notified each time device enters or leaves that pre-defined defined area (this is an untested feature in this review)
Cons
– Map vs Earth views bothered me. The software appears to use its own map service which is not Google Earth, for example. This means it doesn’t offer 2D satellite maps which I think are handy in identifying familiar buildings and environments than just a plain drawn map book type map.
– This is a good and a bad but I put it here. Prey is difficult to find and remove from the device.
Zimbabwean problems Prey can solve or complicate
With widespread internet penetration in Zimbabwe at the moment, right off the bat Prey can help solve the nagging problem of stolen devices from laptops to tablets and phones.
Just about everyone has had themselves or someone they know loosing a valuable device through theft.
Considering that folks must at some point go online for app updates and what not, it’s almost certain some lead of a missing device will come up.
As in my case 11 months later my long forgotten computer showed up.
Prey can also help control the sell of illegally acquired devices.
At a policing level something similar to Prey run by law enforcement itself for the benefit of the general public could be possible, however, after some thought on what follows.
I think Prey was designed with societies in mind where generally devices have a single owner for the duration of their lifespan or at least for the longest time.
In Zimbabwe there is a high device ownership conversion which triggers privacy issues. People buy, sell and trade-in devices left right and center for financial gain or upgrade all the time.
Considering that Prey is very easy to install and incredibly difficult to remove from the device for an average person, many devices will legally exchange hands with active installations.
This means former owners who still control the sold device can literally prey on new device owners in all kinds of ways making Prey a double edged sword in our current environment.
This complicates what initially appears to be an effective solution to a problem.
Overall, baring the above issues, I give the application 4 out of 5 stars.

11 comments
what if the thief just formats the laptop or flashes the tablet, how will prey work
What I thought exactly. If it is removed when the phone is “flashed” then it’s rubbish. In that case you can just use plain Google. If you loose your phone you can just Google “where is your phone and it will be located in seconds.” You can ring it, wipe it,lock it and have it display a custom message.
Exactly my thinking….
the issue with prey is that it is not persistant in term of formating but that is changing. But I have had success when you pack Prey in a custom android rom and prevent formating by enabling FRP Factory reset Prevention. Yes FRP is effective and it is built into the android bootloader. As with PCs flashing custom bios that load programs into memory at boot do the job right but i am yet to acquire the skills or a test machine to burn my fingers on. There are trivial ways to bypass FRP but a patch should arrive soon
I wish this guy would use plain old English instead of trying to slip in Americanisms so that he can be “cool”. You don’t know what I am talking about?
Examples: “How cool is that one year later!”, “…right off the bat…”
Then he comes up with misspelt gems like “Just about everyone has had themselves or someone they know LOOSING a valuable device through theft.” Its so clumsy, because he is obviously educated here. Why does he have to do this? A technical writer should impress his/her audience by the breadth and depth of their knowledge, rather than by how many Americanisms they throw into an article.
Go to hell.
the same to you dogface
In fact after you, cos I was giving a valid opinion, not knowing I am talking to you, dog drollickies
Maybe he has lived in America for a “freaking” long time.
Gramma Nazi out in full force today!
lemme try that now and see how things go. thank you for this info Shoko.